In recent days, everyone has been screened by blackmail, and the last time the whole network was so fearful, it was because of a cute panda!

Panda burning virus
On the 12th, a ransomware called "wannacry" (want to cry) virus, a large-scale invasion of the global computer network, thousands of computers, including 99 countries including China, the United States have been recruited! The hacker locks the data file on the computer and asks to pay $300 equivalent of bitcoin to unlock the file.
Part of the country and more Chinese oil 601857, buy its gas stations suddenly appeared off network around at 0:00 on May 12, can not use Paypal, micro-channel, networking and other CUP card payment, can only pay with cash, a gas station normal business run.
It is worth noting that many universities in China have been affected by this cyberattack. According to China Youth Network, the recent graduation paper season has caused an impact on the education network and campus network of some universities in China, causing many laboratory data and graduation designs to be locked. More than a dozen universities including Shandong University, Nanchang University, Guangxi Normal University, and Dongbei University of Finance and Economics issued notices to remind teachers and students to take precautions.
The situation is still expanding, and public security networks such as Beijing, Shanghai, Jiangsu, Tianjin and other places have also been suspected of having been attacked by viruses.
The symptoms of poisoning are as follows:

Figure
Some media reported that a brokerage information technology headquarters received a notice, the CSRC agencies and associations attached great importance to the blackmail virus incident, requiring brokers to self-examine and prevent and protect, and today (May 14) feedback before 12 noon. It can be seen from the broker's response notice that the broker has developed relevant technical emergency response plans and is already conducting inspections and continuous reinforcement of various business systems. The notice and technical emergency disposal plan are issued by mail, SMS, OA notice, etc. Please kindly remind all departments, branches, subsidiaries, and sales department staff to complete the coordinated inspection and implement the protective measures before noon on the 14th.
Just as everyone began to question the security of Bitcoin and other virtual currencies and the so-called "decentralization", many virtual currency investors and blockchain people told reporters that this ransomware and bitcoin There is no direct relationship in itself, and hackers demand ransom payments in bitcoin, which is precisely the advantage of Bitcoin's globalization, decentralization and anonymity when paying for transfers.
"In a sense, this global extortion is more like an 'application scenario' for Bitcoin," said a senior virtual currency investor.
Why is Bitcoin?
In fact, this hacking software has existed since 1980. According to Cyence, hackers often target hospitals, businesses, and other places with low levels of informationization. The average ransom payment per order is between $500 and $1,000. And because of the existence of Bitcoin, global extortion has become more cost-effective and less risky than crimes such as stealing credit cards.
A number of Bitcoin investors said that the reason for the blackmail virus attack is not directly related to Bitcoin itself. The industry is worried that Bitcoin will be "demonized". The reason why hackers demanded to pay ransom in bitcoin is that they have taken advantage of the advantages of its global transfer and remittance, thus becoming the chosen means of payment.
Bitcoin investors generally believe that Bitcoin is used for extortion because Bitcoin not only has advantages over other traditional payment instruments, but is also the best choice among other virtual currencies. First of all, Bitcoin has certain anonymity, which is convenient for hackers to hide their identity. Secondly, it is not subject to geographical restrictions and can be collected globally. At the same time, Bitcoin has the characteristics of “decentralizationâ€, which allows hackers to automatically handle victims through programs. ransom. Compared with other digital currencies, Bitcoin currently has the largest market share and has the best liquidity, so it has become a hacker's choice. This is similar to the logic behind the fact that criminals in the world like to use dollar bills.
However, there are also views that Bitcoin's above advantages are actually flawed, and Bitcoin's transaction processing efficiency and anonymity are not optimal. In terms of anonymity, although bitcoin transactions are anonymous, the bitcoin trader identity is actually traceable.
“The transaction information of Bitcoin is actually transparent. Although the identity information will not be transmitted when paying, the IP address of the user when paying is checkable. The characteristics of Bitcoin's entire network accounting make it every transaction. All billing nodes can see the contents of their transactions. We can query specific transaction information such as transaction volume on websites such as blockchain.info, such as one of the payment addresses announced by the hacker, as of the evening of May 13 A total of 23 bitcoin remittances were received, and each payment was around 0.17 bitcoins, totaling about 4.26 (worth about $7,455). According to the case that FB I has handled, unless the user is good at anti-tracking (such as using Tor) ), otherwise most people can still find identity." A senior blockchain person told reporters, however, if the extortionist does not use and trade after receiving the bitcoin, then it is still unable to track its identity.
In fact, in addition to extortion, crimes in some dark networks, such as money laundering, illegal transactions, and escaping foreign exchange controls, also take advantage of the anonymity of Bitcoin. For example, in October 2013, Silk Road, an electronic trading platform that used Bitcoin for anonymous illegal trading, was seized by various law enforcement agencies in the United States. At the same time, 26,000 bitcoins were seized, which was worth about $3.6 million. The founder and operator of the platform, Ross Williams Ublich, a 29-year-old young man from a non-professional degree who is pursuing a degree, is active on the Internet as another member of Dread Pirate Roberts. In just two years, Silk Road has become the largest black market in the online world, with nearly 1 million customers and sales totaling $1.2 billion. On this platform, the service covers fake passports, fake driver's licenses, illegal intrusion into the system and access to information, buying and selling drugs, weapons, pornography, etc., but all transactions are completed through bitcoin payments. It is the use of the anonymity of Bitcoin that criminals “perfectly†avoid the possibility of monitoring the flow of money through bank card transaction records.
In addition, Bitcoin is also used to launder money and illegal transfer of assets, buy bitcoin in the national currency, sell it on foreign trading platforms, and then take it out in US dollars, and the asset transfer can be completed in a few minutes.
Special analysts of the Firecoin Network believe that since April, the internationally favorable news of bitcoin recognition has spurred the rise of Bitcoin. After Japan’s payment service amendment bill, which supports bitcoin payments, came into effect on April 1, the legality of virtual currency payment methods such as Japanese Bitcoin was recognized, and 260,000 stores in Japan will accept bitcoin payments.
In recent days, the surge in bitcoin has also been closely related to the US Securities and Exchange Commission's review of the Bitcoin ETF date on May 10. If the Bitcoin ETF is approved for listing by the US Securities and Exchange Commission, it means that Bitcoin's global investment position will increase.
Australia has announced that it will treat Bitcoin as currency on July 1, 2017 and will abolish Bitcoin Goods and Services Tax. Bitcoin traders and investors buying and selling bitcoin through regulated exchanges and trading platforms will no longer be taxed.
What should I do after the computer is recruited?
The outbreak of the ransomware is a new family called "wannacry", which is currently unable to decrypt files encrypted by the ransomware. The ransomware quickly infected a large number of hosts around the world by exploiting the SMB vulnerability MS17-101 (Eternal Blue) based on 445 port propagation spread. Microsoft released the vulnerability patch in March this year.
Safety advice:
1. Update the latest operating system patches in a timely manner.
2. Turn off the ports that the operating system does not need to open, such as 445, 135, 137, 138, 139, etc., and turn off network sharing.
3. Back up important file data regularly.
The influence of this matter has exceeded market expectations. It will be worthy of great attention in the secondary market. The network security sector is the biggest positive segment of the event.
Here are some of the stock information of the network security sector, for your reference:
1. NSFOCUS 300369, buy
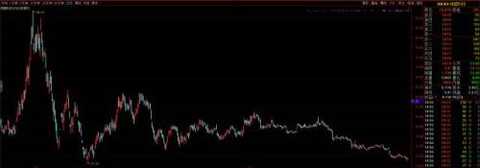
trend
Main: research and development, production, sales and provision of professional security services for information security products.
Finance: The unaudited net profit was -5,042.117 million.
2. Guardian 002268, buy
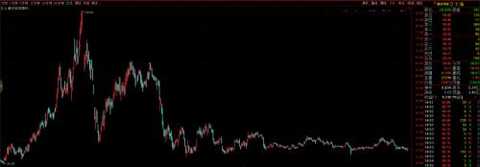
trend
Main: R&D, production, sales, security integration and security services for information security products and systems for the civilian market.
Finance: The unaudited net profit was -10,195,270 yuan.
3. Beixinyuan 300352, buy
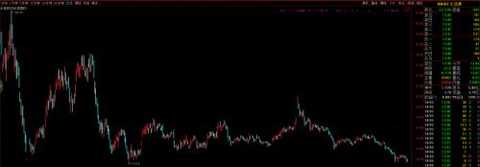
trend
Main: research and development, production, sales and technical services of information security software products.
Finance: The unaudited net profit was 823,500 yuan.
4. Blue Shield shares 300297, buy
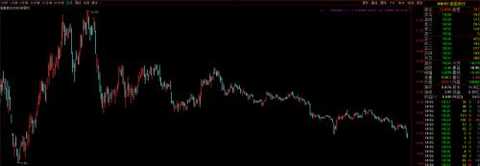
trend
The company focuses on the enterprise-level information security field and builds a complete business system based on information security products, covering information security integration and information security services, and relies on established technology research and development, professional qualifications, comprehensive service capabilities, customer resources and talents. Such as the competitive advantage of love base, net worth, information, has been rated as the National Torch Program key high-tech enterprises, national high-tech enterprises, is currently a member of the International Cloud Security Alliance (CSA).
The above four stocks are only information security concept stocks. The stock market is risky and investment needs to be cautious. The stocks involved in the article do not constitute investment advice.
Fitness Vest,Fitness Yoga Vest,Functional Dry Fit Yoga Wear,Womens Yoga Vest
Shaoxing Yizhong Textile And Garment Co.,Ltd , https://www.yizhongsport.com